VMware: vCAC critical remote privilege escalation vulnerability
Summary
VMware vCloud Automation Center (vCAC) product updates address a critical vulnerability in the vCAC VMware Remote Console (VMRC) function which could lead to a remote privilege escalation.
Relevant releases
vCloud Automation Center 6.x without patch
Problem Description: VMware vCloud Automation Center remote privilege escalation
VMware vCloud Automation Center has a remote privilege escalation vulnerability. This issue may allow an authenticated vCAC user to obtain administrative access to vCenter Server.
This issue is present in environments that use the "Connect (by) Using VMRC" function in vCAC to connect directly to vCenter Server. Environments that exclusively use vCloud Director (vCD) as a proxy to connect to vCenter Server are not affected.
At this time the issue is remediated by removing the "Connect (by) Using VMRC" functionality for directly connecting to vCenter Server. Deploying the provided patch will remove this functionality.
VMware is working on a secure solution that will restore this functionality. Customers may continue to use the "Connect (by) Using RDP" or "Connect (by) Using SSH" options for remote desktop management as they are not affected by this issue.
The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the identifier CVE-2014-8373 to this issue.
Column 4 of the following table lists the action required to remediate the vulnerability in each release, if a solution is available.
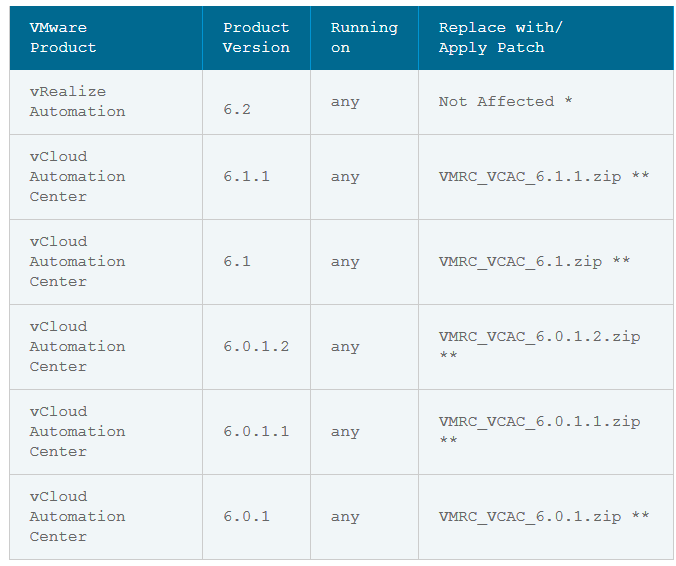
Solution
Please review the patch/release notes for your product and version and verify the checksum of your downloaded file.
vCloud Automation Center 6.x
Downloads and Documentation:
http://kb.vmware.com/kb/2097932
References
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-8373
More information: VMware
Thanks for this one, had same issue 🙂 used this solution